Endpoint Encryption Techniques
- Transparent Volume-based Encryption (On-the-Fly Encrption):
In this mode, the product doesn’t care about the file extension or file format. It’ll rather provide the target user with a virtual volume so that every file being copied or stored in that volume will automatically and transparently get encrypted. The user is required to enter a secret-password to access this virtual volume, and in cases where the password is incorrect the virtual volume will remain non-accessible. If the password attempts reach the criterial number (that defaults to 5), the virtual volume gets locked, so that a system restart is required.
By the way after the entered password is accepted, the user can normally read and copy the files everywhere, while the copying of sensitive files (by extension) in external storages is prohibited.
- Transparent File-based Encryption: In this mode, the encryption is performed with an eye to the selected criteria (by the security staff) for the file or its metadata. So only the files matching that criteria are encrypted in this mode, while leaving the other files untouched in their plain-formed version.
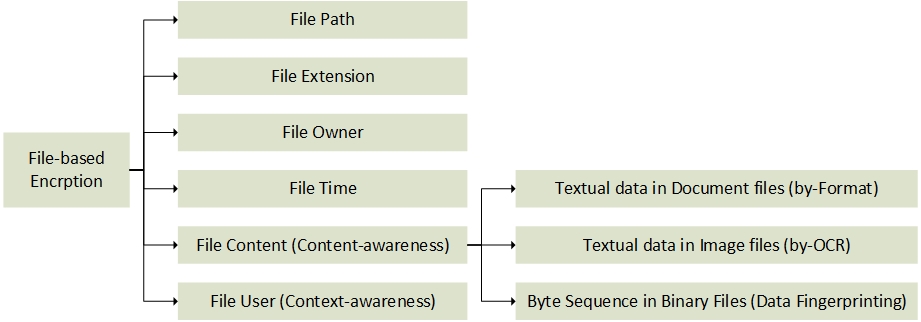
content detection teqniques in Netcognize Endpoint DLP
The possible criteria in this mode are categorized in the following:
- File Path: File Extension: The file(s) matching the specified extension are encrypted.
- File Owner: The file(s) matching the specified creating-owner are encrypted.
- File Time: The file(s) matching the specified timestamp are encrypted.
- File Content: The file(s) containing a specified data phrase or criteria are being encrypted. This option is best functioning when used against document or image files.
- File User: The file(s) containing a specified data phrase or criteria are being encrypted, and they are only decrypted and accessible to the specified users, while remain encrypted for other users.
